Delegate Key Signing
All events in the Towns Protocol are signed by an ECDSA wallet key pair. Users and nodes can both send events using a process referred to as delegate signing that allows for events to be signed by a separate device linked to the primary wallet. Delegate signing therefore opens the protocol to allow events from linked devices the user has custody of. Towns Stream Nodes validate the signature prior to processing an event that is for example being added to a stream usingaddEvent RPC method.
Why ECDSA ? First, ECDSA elliptic curve derived keys have been proven to be less susceptible to breaking than earlier algorithms such as RSA. Secondly, ECDSA keys are smaller at 256-bytes and less cpu intensive to generate signatures than asymmetric or RSA keys. Since Towns Stream Nodes validate and store signatures in storage for each event, using ECDSA signatures saves on cpu and disk space.
Delegate Signature Protocol Rules
The logic dictating how a Towns Stream Node should process delegate signatures on the critical path of a request is described inprotocol.proto and defined in delegate.go.
Events sent over RPC to a Towns Stream Node are sent with a message Envelope that includes several fields used to validate the sender.
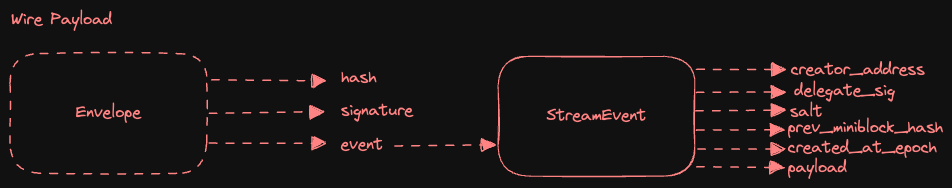
- signature : For the event to be valid, the signature on the
Envelopemust match theEventcreator_address or be signed by the same address implied byEventdelegate_sig. - creator_address : This is the wallet address of the creator of the event, which can be a user or a Towns Stream Node.
- delegate_sig : Optional field that allows events to be signed by a device keypair linked to the user’s primary wallet.
If a delegate signature is present on an event, the event is only valid if either the creator_address matches the delegate_sig’s signer public key or if the delegate_sig signing public key matches the key implied by Envelope.signature.
Delegate Signature Validation
Each event on a Towns Stream Node is parsed and validated as follows.Unmarshal Bytes
Events are stored as bytes in Towns Stream Node storage and transmitted as bytes over the wire.
All events are unmarshalled first and then parsed to run a series of validity checks prior to storing those events.
Check Delegate Signature
Once the hash is confirmed as valid for the event, the hash along with the envelope signature is used to recover the signer public key.
Event creator wallets used to sign events are assumed to be created as Ethereum wallets. Therefore,
secp256k1 algorithm is used to validate signature and sign. Towns Stream Nodes use a hardened version of this algorithm found in go-ethereum package. Node Delegate Events
Towns Stream Nodes are created with an ECDSA wallet used for identity and so can create events destined for streams in the network just like users using their Ethereum wallet as a primary wallet or another linked wallet created using ECDSA. Nodes create new wallets usinggo-ethereum crypto tools in the following function.

